ZYMKEY ZERO
The essential hardware security module for Raspberry Pi
- Easy to integrate plug-in module
- Seamless integration with Bootware
- Hardware root of trust
- File system encryption
- Secure key generation & storage
- Data encryption & signing
- Perimeter tamper sensors
- Measured system identity & authentication
- Real time clock
SD card protection made easyEssential security for Raspberry Pi
Removing an SD card and copying contents is easy, especially for unattended devices deployed outside the security of a physical building. ZYMKEY4 provides essential physical and digital security features to protect against such real world exploits.
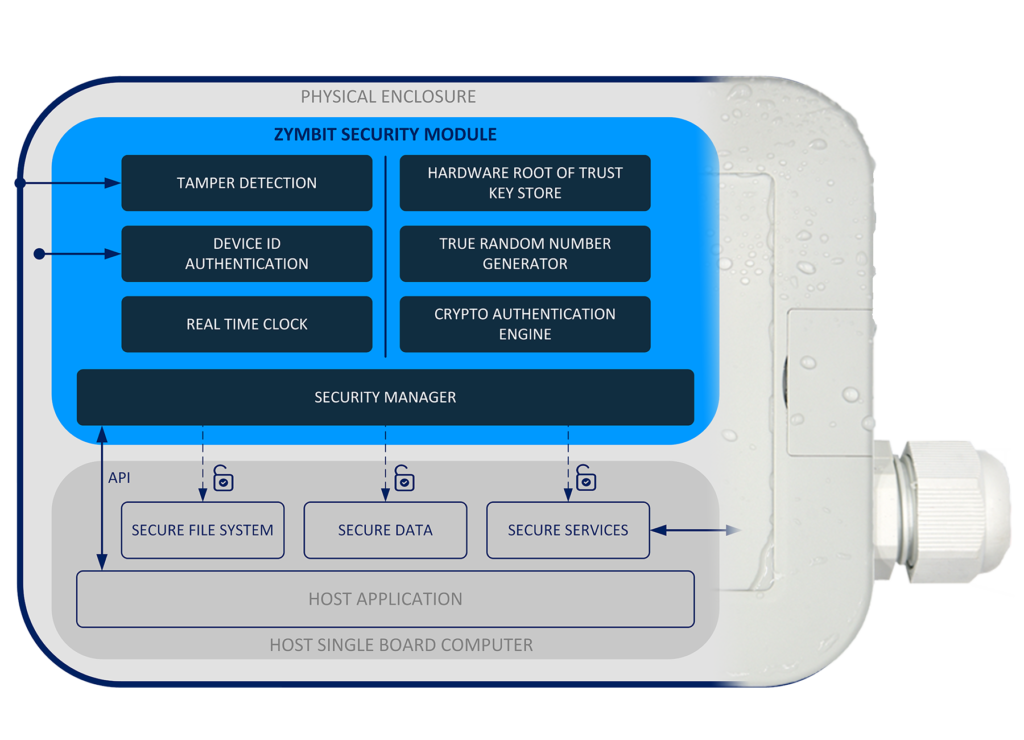
FILE SYSTEM ENCRYPTION
KEY STORAGE & GENERATION
CRYPTOGRAPHIC ENGINE
MEASURED SYSTEM IDENTITY
PHYSICAL TAMPER SENSORS
DATA ENCRYPTION & SIGNING
ULTRA LOW POWER
REAL TIME CLOCK
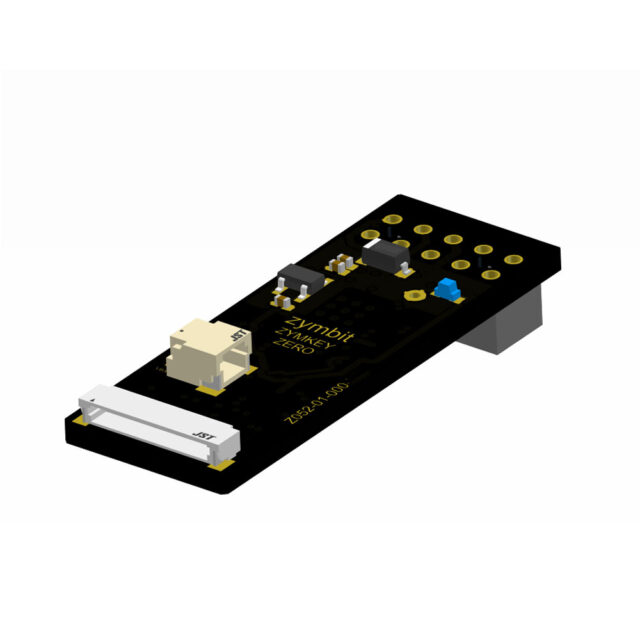
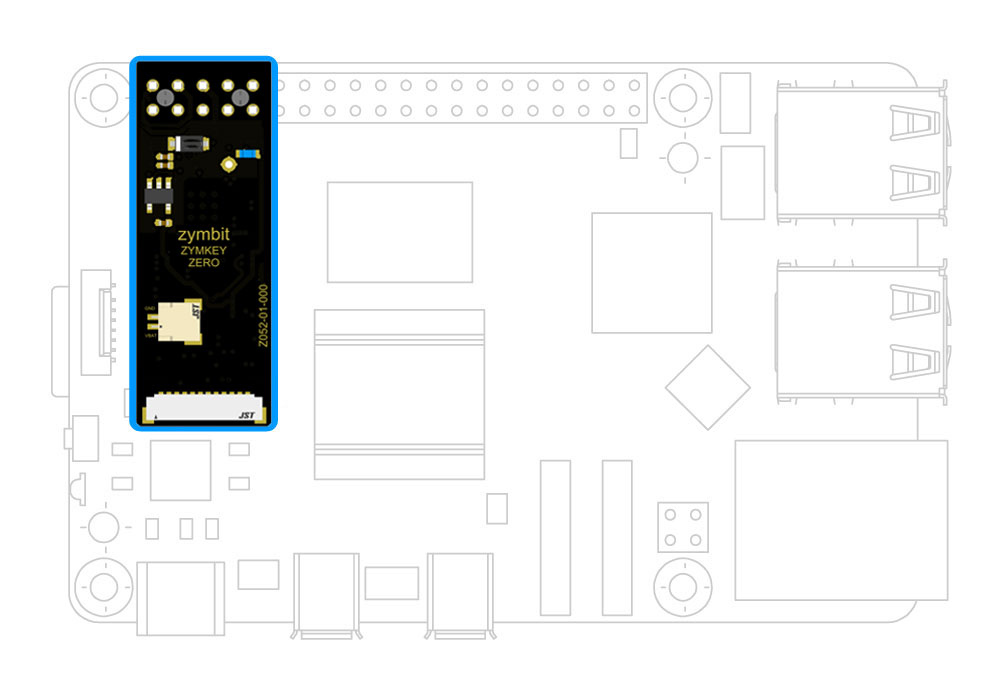
Easy to integrate module
- Plugs on to GPIO headers of Raspberry Pi
- Uses GPIO4, I2C, +5V, GND. (can be remapped)
- APIs in Python, C++, C.
File system encryption
- Encrypt root file system with dm-crypt.
- Protect data, applications and credentials.
- ZYMKEY integrates seamlessly with LUKS key manager.
- Step-by-step guide with prewritten scripts that streamline the process.

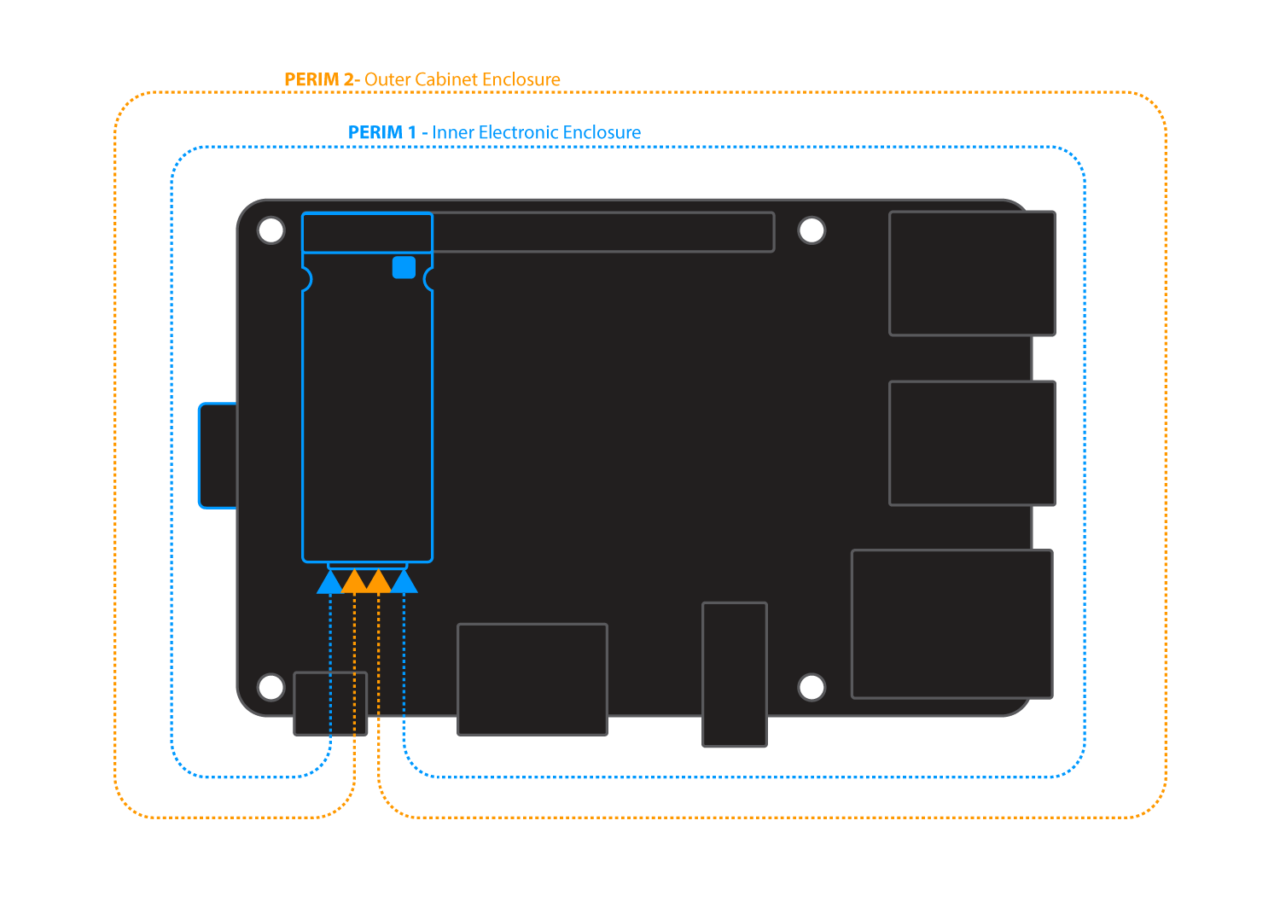
Perimeter tamper detect
- Two independent perimeter circuits provide layered protection.
- User configured policies and actions.
- Notify or destroy keys on perimeter-breach event.
- Continuous operation with onboard battery.
Layered security with hardware root of trust
Zymbit security modules provide multiple layers of physical and digital protection for your digital assets, managed through a simple API.

Easy integration with AWS
TLS Client Certificate Authentication
- Generate Zymkey secured client certs.
- Bring Your Own Certificate or use AWS.
- Attach custom policies.
- Secure connect client authenticated TLS
Just In Time Client Registration
- Simplifies large scale fleet deployments
- Lambda function client registration
Manufacturing tools
Zymbit manufacturing tools and services help you transition to volume manufacturing quickly and securely.
Specifications
| Private / public key pairs | 3 |
| Cryptographic Services | TRNG (NIST SP800-22) ECC NIST P-256 (secp256r1) ECDSA (FIPS186-3) AES-256 (FIPS 197) |
| Tamper Sensors | 2 x Perimeter breach detection circuits Main power monitor |
| Software API | Python, C++, C |
| Physical Format | Plug in mini-hat (pins 1 - 10) |
| Dimensions | 39.0 x 14.0 x 5.3 mm 1.53 x 0.55 x 0.21 Inches |
| Board Connectors |
GPIO: 5x2pin header, 0.1inch Perimeter: 12pin JST 0.8mm receptacle (mates with JST 12SUR-32S) Battery: 2pin JST 0.8mm receptacle (mates with JST 2SUR-32S) |
| Communication | I2C, default address, user changeable GPIO4, user changeable |
| Production mode lock | Software API command |
| Measured system identity & authentication | Standard factors include RPI host, SD card, Zymkey |
| Data encryption & signing applications. | Encrypt root file system with dm-crypt, with LUKS key manager hook Encrypt data blobs with "zblock" function Encrypt data in flight with OpenSSL integration |
| Real time clock | 24-36 month operation, application dependent, 5ppm accuracy. |
| Backup battery | Used for RTC and perimeter circuits Requires JST connected coin cell, RPI 5 RTC battery , or similar, (not included) Recommend |
| Backup battery monitor | Yes |
| Last Gasp battery removal detection | No |
| OEM Custom features | Contact Zymbit |
| Example Cipher Suites | AWS-IOT | TLS_ECDHE_ECDSA_AES256_SHA MS-AZURE | TLS_ECDHE_ECDSA_AES_128_GCM_SHA256_P256 |
| Accessories & related products | Backup battery, perimeter cables |
| Warranty | 18 months |
| Compatibility | Pi Zero, 4, 5 |
Documentation
Using Product >
- Getting started
- Software APIs – python, C, C++
- Tutorials
- FAQ & troubleshooting
Conformity Documents >
- EU Declaration of Conformity
- FCC Declaration of Conformity
- RoHS/Reach Declaration of Conformity
- California Prop 65 Declaration of
CAD Files >
- Mechanical dimensions
- Step model
Manufacturing Tools >
- Secure high speed encryption appliance
- Programming and provisioning
Need help choosing product?
Explore and choose the best Zymbit product for your application. If you have questions or need something custom then were ready to help.
I'M READY TO BUY
Zymbit products are available from major distributors around the world, or directly from our webstore.
I HAVE QUESTIONS
If you need help with your application, or want to discuss a custom solution then contact us today.