Less complexity, more resilient deployments
Bootware manages the complexity of binding together operating system, boot chain and bare metal–into a robust and maintainable compute platform. Bootware delivers highly secure and reliable deployments while maintaining an agile development environment
Bootware binds software and hardware together into a robust, cryptographically linked compute platform—from secure boot to kernel to application and containerized work loads.
Core device security
Bootware binds and anchors the chain of trust to bare metal security and supervisory functions within a device.
When used with Zymbit hardware, Bootware supports a layered trust model, with autonomous validation of physical device integrity, tamper sensors for environmental and power attacks.
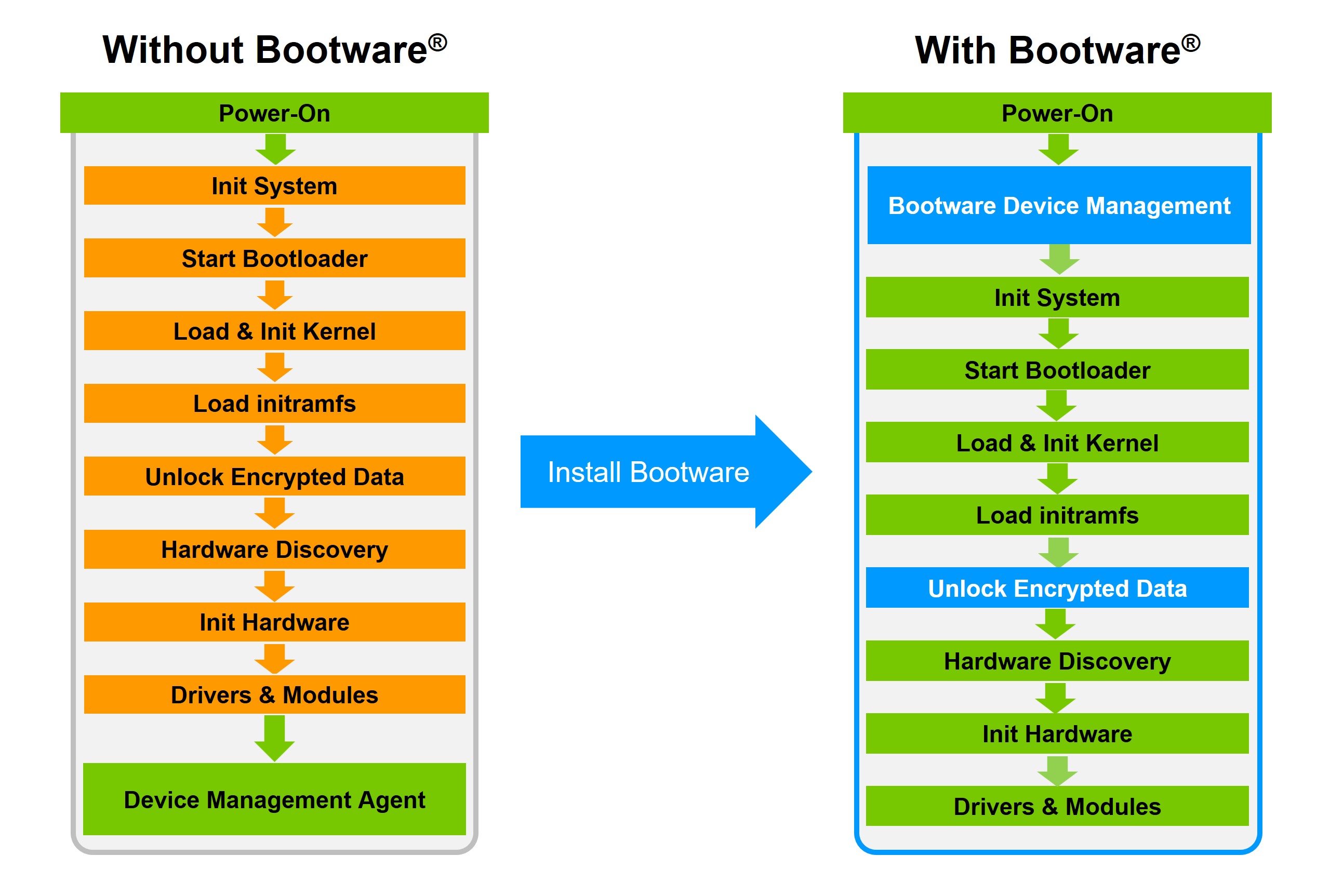
Robust boot schema
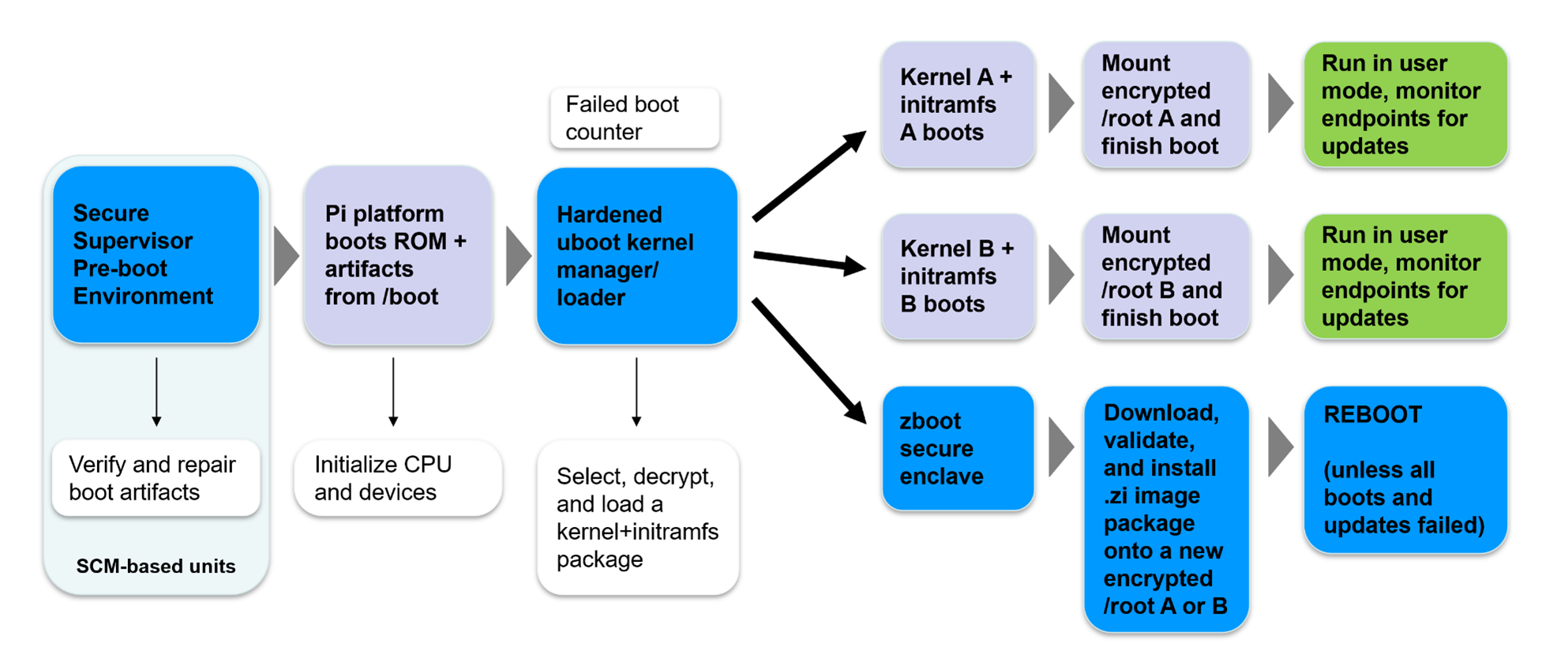
Bootware manages the device from the moment it is powered on.
Starting very early in the boot process ensures that the system has successfully booted into user mode. Bootware is able to manage and recover the system without relying on a functional bootable Linux image.
Bootware supports Ubuntu and Raspberry Pi OS as standard. Contact Zymbit for support of other Linux distributions.
Ironclad updates
Zymbit A/B update schema is built upon Zymbit’s hardened boot chain, which ensures consistent integrity and reliability. Other A/B update schema rely on user mode functionality which can be compromised.
A/B image management works seamless with encrypted file systems, signed images and updates.
Fallback and recovery options.
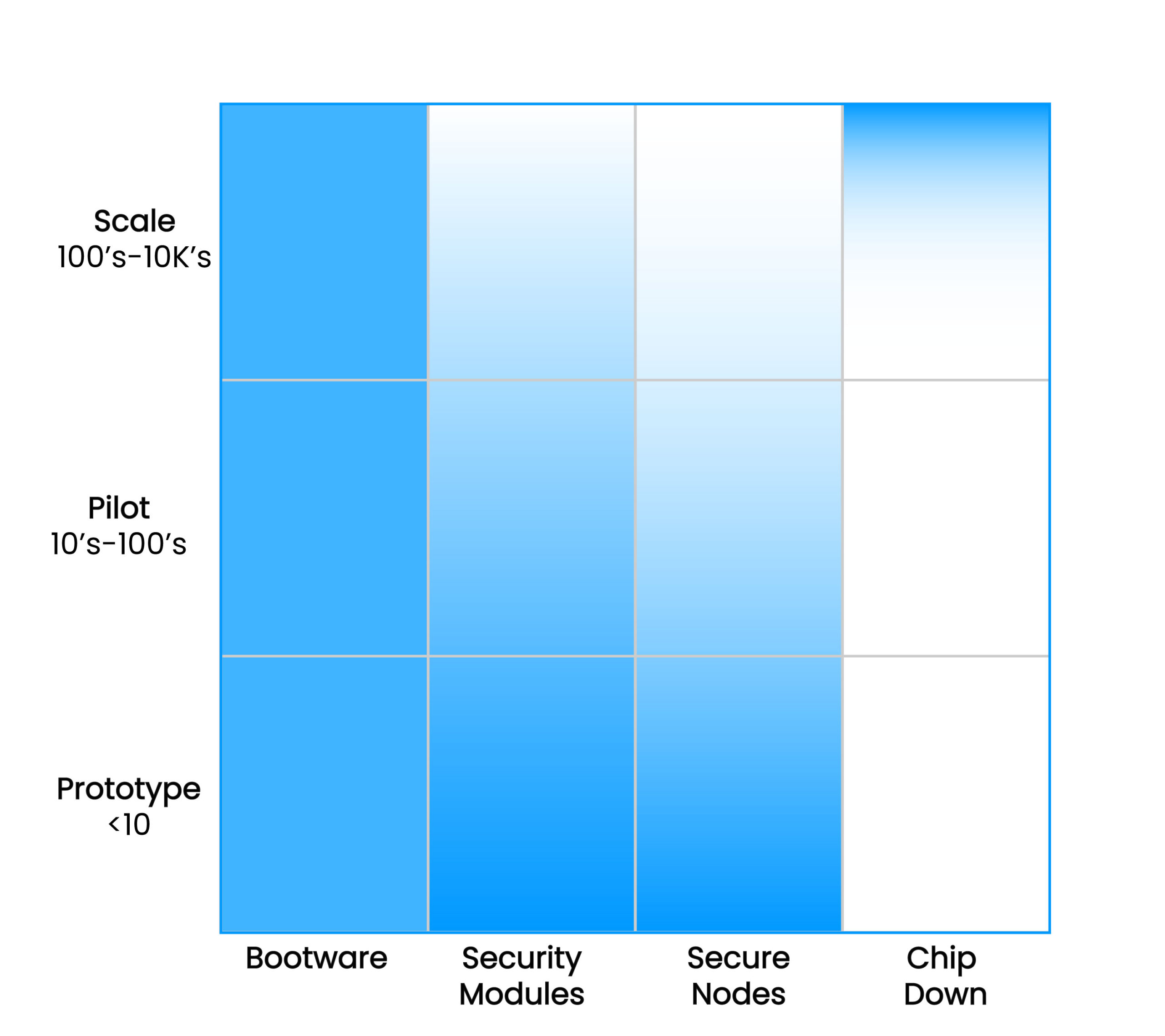
Easy to integrate at any scale
Building core resilience into Linux devices doesn’t have to be complex or require extensive planning. Bootware integrates seamlessly with Zymbit secure hardware at any stage, deploys flexibly, and scales cost-effectively as your business grows.
Step by step technical tutorials
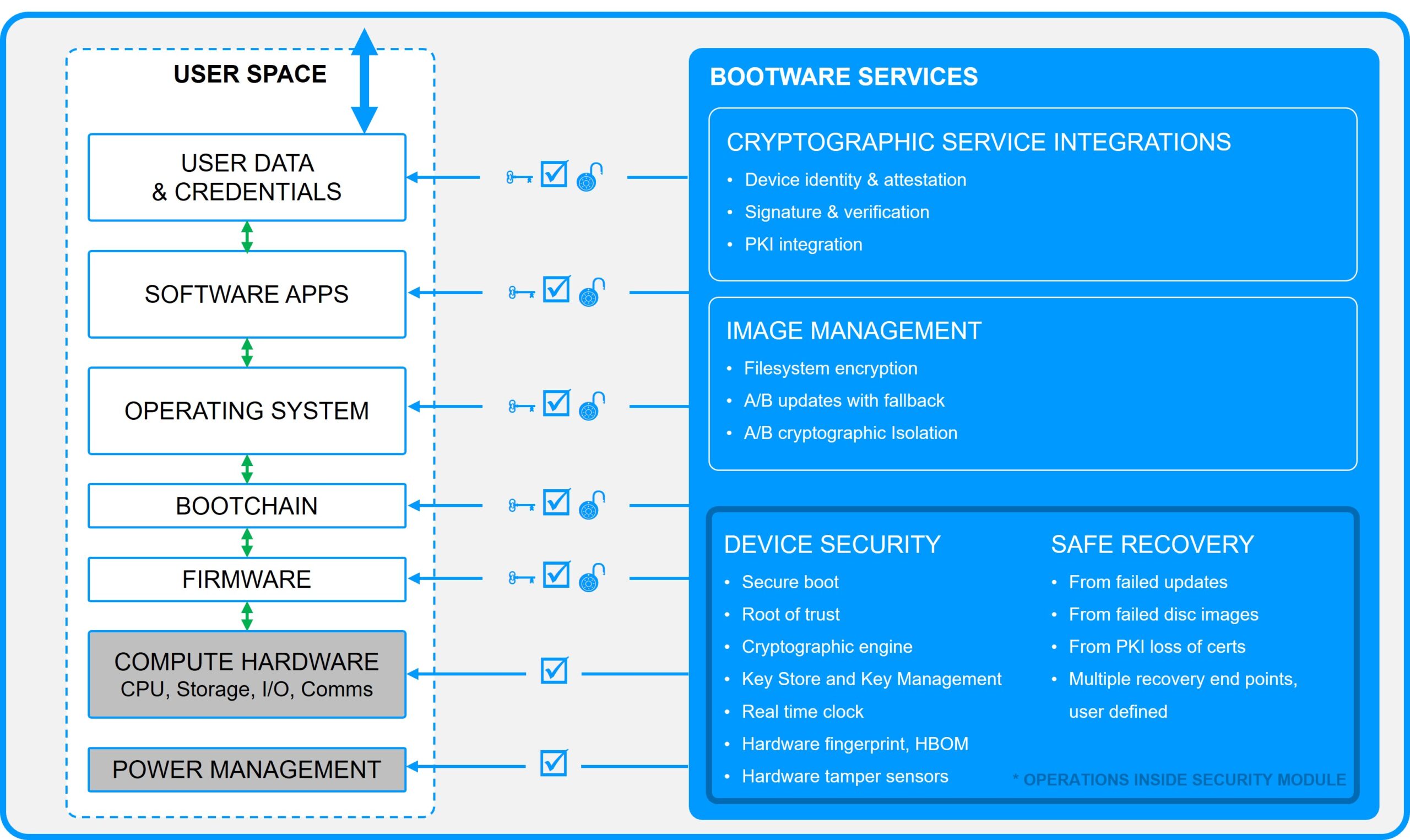
Bootware services
A/B updates with cryptographic isolation
Robust update schema backed by secure silicon.
- Keep devices current with frequent operational and security updates.
- A/B filesystems are cryptographically isolated, including boot artifacts.
- Updates are supervised by an independent security controller.
- Roll back to a stable filesystem in case of failed or compromised updates.
Encrypted filesystem and kernel
Protects your data, IP and credentials from unauthorized access.
- Data and kernel are encrypted with keys managed in the HSM.
- Keys are scrubbed upon device penetration to prevent access to data.
- Works seamlessly with A/B updates.
Automatic recovery from failed updates
Minimize operational downtime when A/B updates inevitably fail.
Loss of network access, loss of power and incorrect signatures, are a few common failure modes. When updates fail it is essential that a device has the possibility to recover to some trusted operational state, and preferably without human intervention, remote or local.
Bootware supports three levels of trusted recovery.
- Failed update of Image-A > revert to Image-B.
- Failed Image-B > revert to Safe Recovery mode.
- Failed Safe > revert to user intervention.
Signed images and updates
Ensures that all update images come from a known and verified source, and have not been tampered with.
- Only devices with the correct HSM keys will be able to authenticate the source and pull these secure updates.
Key storage in secure silicon
Reduces the risk of exposing cryptographic keys through physical access and sideband attacks.
- Cryptographic keys are created, managed and stored in a special purpose secure element with grid protection.
- Logical and physical access is restricted through multiple layers of cryptography, hardware and tamper sensors.
Supervised boot with user defined artifacts
Reduce the risk of compromised boot chains and bricked devices.
- Zymbit S2, S3 level devices use an independent security controller to supervise the boot process.
- Boot artifacts are individually verified for integrity and authenticity against a user defined manifest.
- Security policies can be put in place to prevent failed and compromised updates.
Seamless integration with Raspberry Pi OS and Ubuntu
Develop and deploy using popular Ubuntu and Raspberry Pi OS tools.
- Push secure updates to systems with Debian based OS.
- Support for custom kernel builds.
- Switch between Bullseye and Ubuntu 22.04 during development.
Supported on Zymbit secure compute products
Bootware services are available on a wide range of Zymbit professional components.
- Security Modules
- Secure Edge Nodes
- Reference designs & developer kits
- See Bootware enabled Zymbit products
Pricing
Check out Bootware Core for free!
Choose the plan that fits your needs.
Prototyping
Free
Bootware Core
- A/B updates
- Encrypted filesystem
- Encrypted kernel
- A/B cryptrographic isolation
- Key storage in secure silicon
- Supervised boot
- Multiple artifacts & policies
Support
SL0 Self service, community
Pilot
$2400/year
Bootware Core
- A/B updates
- Encrypted filesystem
- Encrypted kernel
- A/B cryptrographic isolation
- Key storage in secure silicon
- Supervised boot
- Multiple artifacts & policies
Bootware Premium
- Baremetal recovery
- Zero touch provisioning
- Standard integrations
- Unlocked pilot hardware
Support
SL1 Best effort
Scale
$12/device/year
Bootware Core
- A/B updates
- Encrypted filesystem
- Encrypted kernel
- A/B cryptrographic isolation
- Key storage in secure silicon
- Supervised boot
- Multiple artifacts & policies
Bootware Premium
- Baremetal recovery
- Zero touch provisioning
- Standard integrations
- Custom integrations
- Custom hardware support
Support
SL2 Best effort, priority
Enterprise
Quoted Pricing
Bootware Core
- A/B updates
- Encrypted filesystem
- Encrypted kernel
- A/B cryptrographic isolation
- Key storage in secure silicon
- Supervised boot
- Multiple artifacts & policies
Bootware Premium
- Baremetal recovery
- Zero touch provisioning
- Standard integrations
- Custom integrations
- Custom hardware support
Support
SL3 Service Level Agreements
Documentation
Ready to try Bootware?