Most people agree that a $1M is worth protecting.
Typical commercial applications contain many man-years, sometimes man-decades, of investment in software development. In business terms this represents a tangible IP asset that has the potential to generate recurring revenues for years to come. If you lose exclusivity of that asset – by someone copying it – then your business will lose valuable revenues.
The threat
SDcards are vulnerable to exploitation, particularly when the host product is placed in distant locations, unattended and serviced by unknown parties. The main things to consider are:
Which digital assets do I need to protect?
- Applications
- Data
- Keys
What attack vectors are likely?
- Remote access copy of contents.
- Physical removal and copying of card.
- In-situ copy of contents using software access.
- In-situ ‘sniffing’ of contents using physical access.
Learn more about real cyberphysical attack exploits >
Zymbit solutions
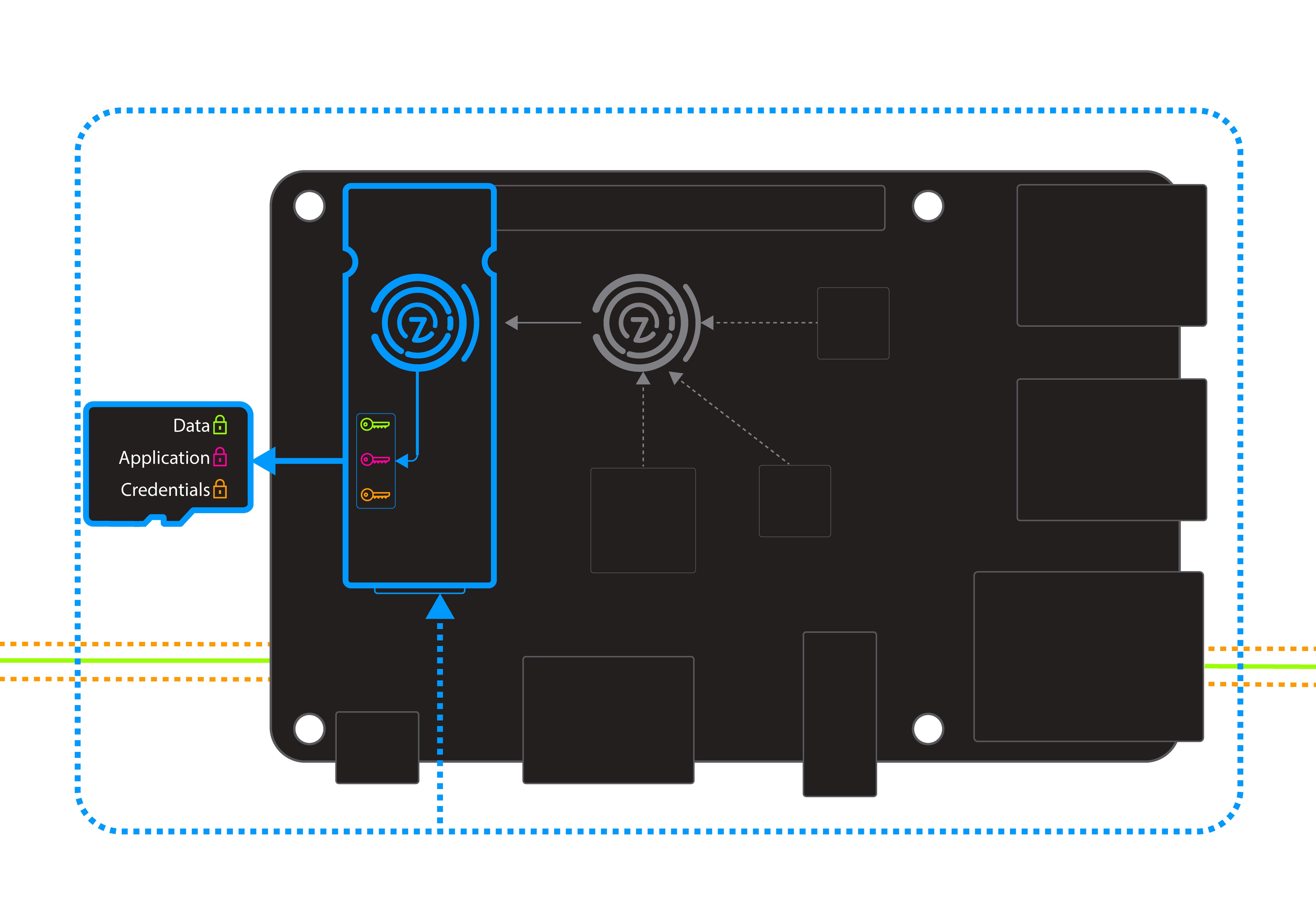
Zymbit security modules will protect SDcard contents from physical and digital exploits.
Access to SDcard data, applications and keys is granted only when two conditions are true:
- The physical integrity of the system is tamper-free – no breach of perimeter, power events, shock events.
- The measured-system-fingerprint authenticates correctly. If any of the measured system components (host computer, SDcard, zymbit) have changed, then the system will not grant access.
_______________________________________________________________________________________________
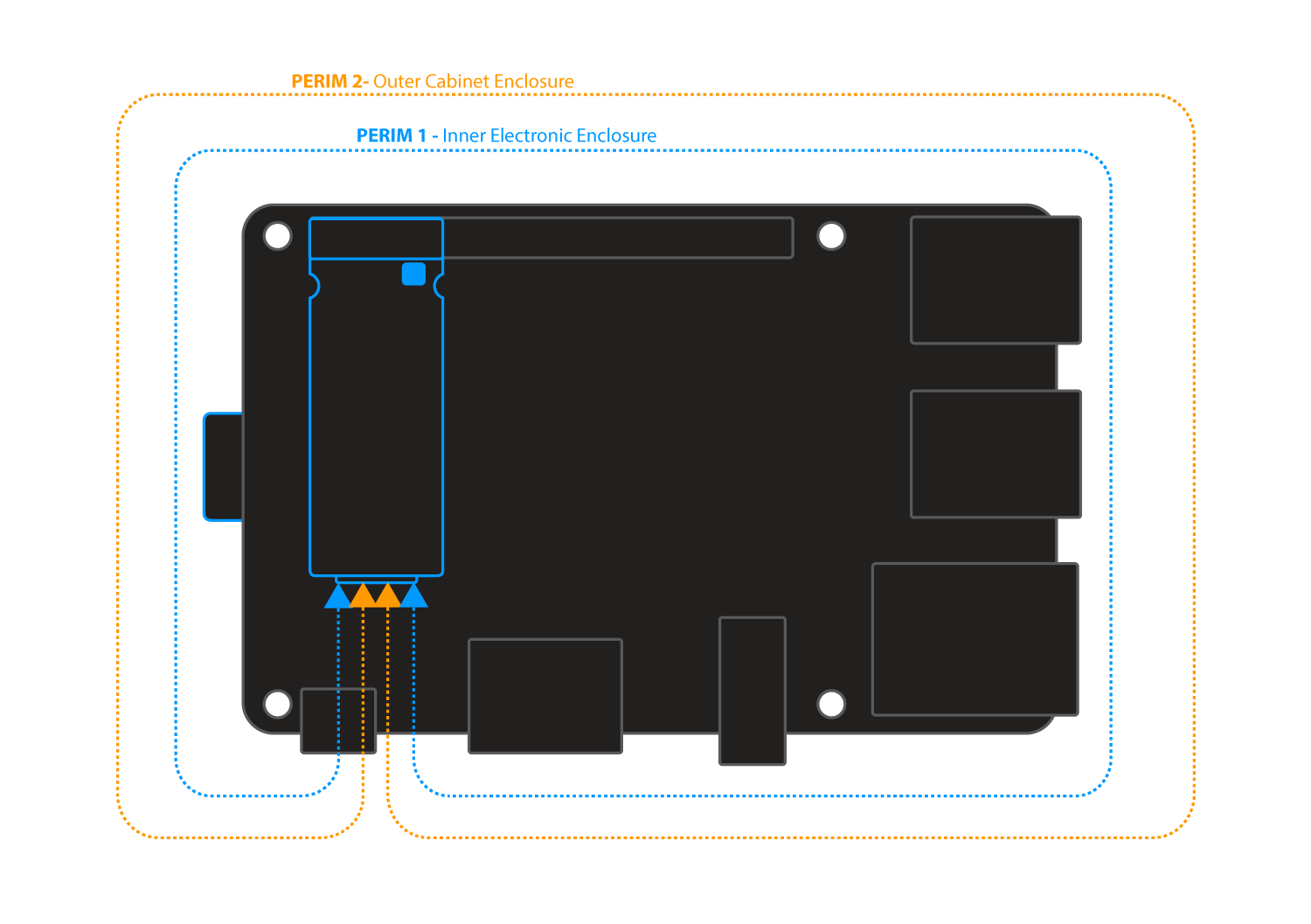
Physical system integrity using tamper sensors and response.
Physical security is often overlooked for unattended edge devices and equipment. Yet everyone recognizes that a computer server should be secured in locked room, and a personal computer should not be left unattended.
Zymbit security modules support multiple tamper sensors which can be configured to autonomously monitor external events, and to which different tamper-response policies can be assigned.
Tamper sensors (model dependent)
- Two perimeter circuits
- Power supply monitor
- Temperature monitor
- Shock accelerometer
Tamper-response policies:
- Ignore event
- Notify host
- Destroy key material
_______________________________________________________________________________________________
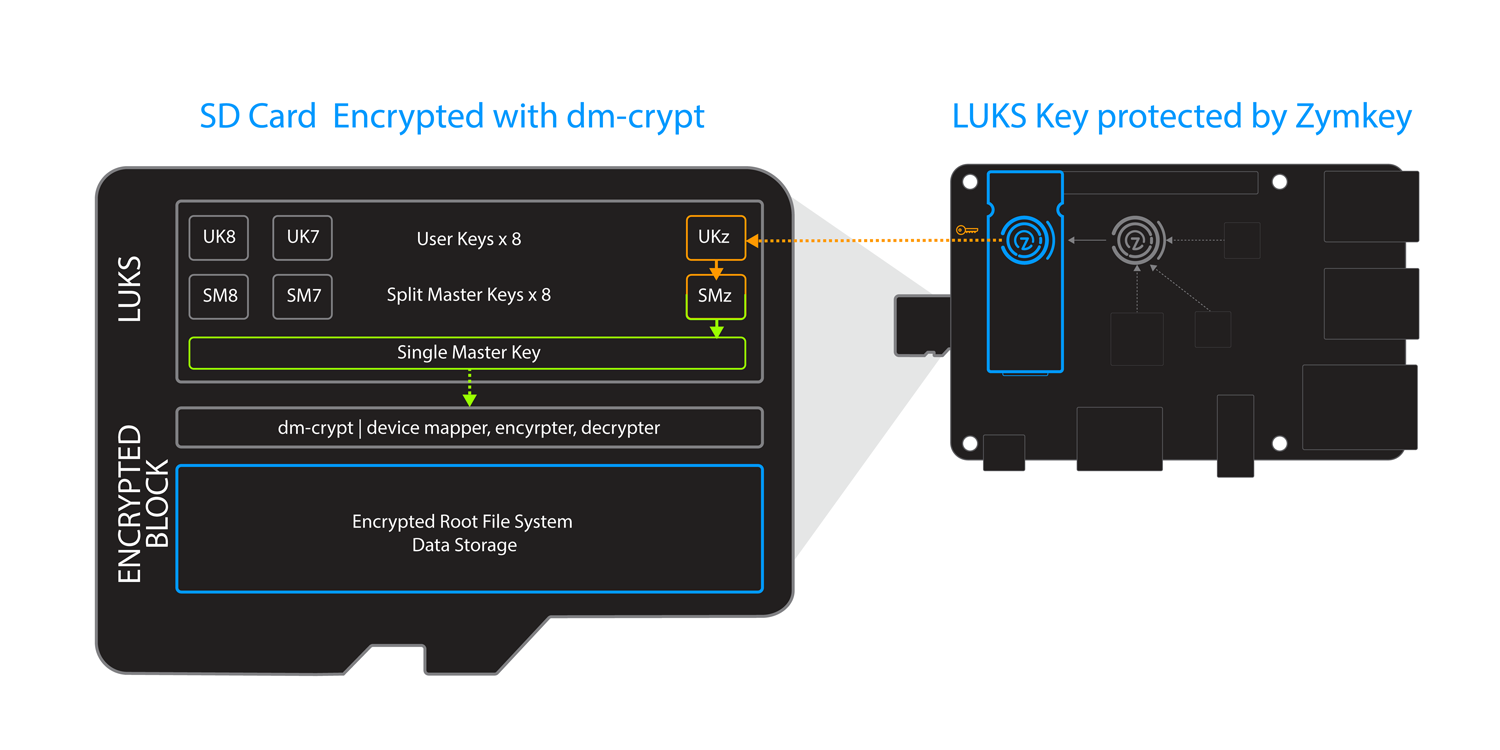
Root file system encryption
Additional layers of protection provide increasing resistance to attacker. Encrypting a root file system is widely used method for securing digital assets in physical media. Most personal computers offer disk encryption, and its the norm in enterprise grade servers and storage.
When implementing encryption its usually best to follow well established cryptographic standards and methods: they are generally well understood, tested and auditable, which makes them a measurable and reliable source of security.
Zymbit secure modules provide a seamless integration with the popular dm-crypt disk encryption sub-system found in Linux kernels. Specifically they manage one (or more, model dependent) of the User Keys used in the Linux User Key Setup (LUKS)
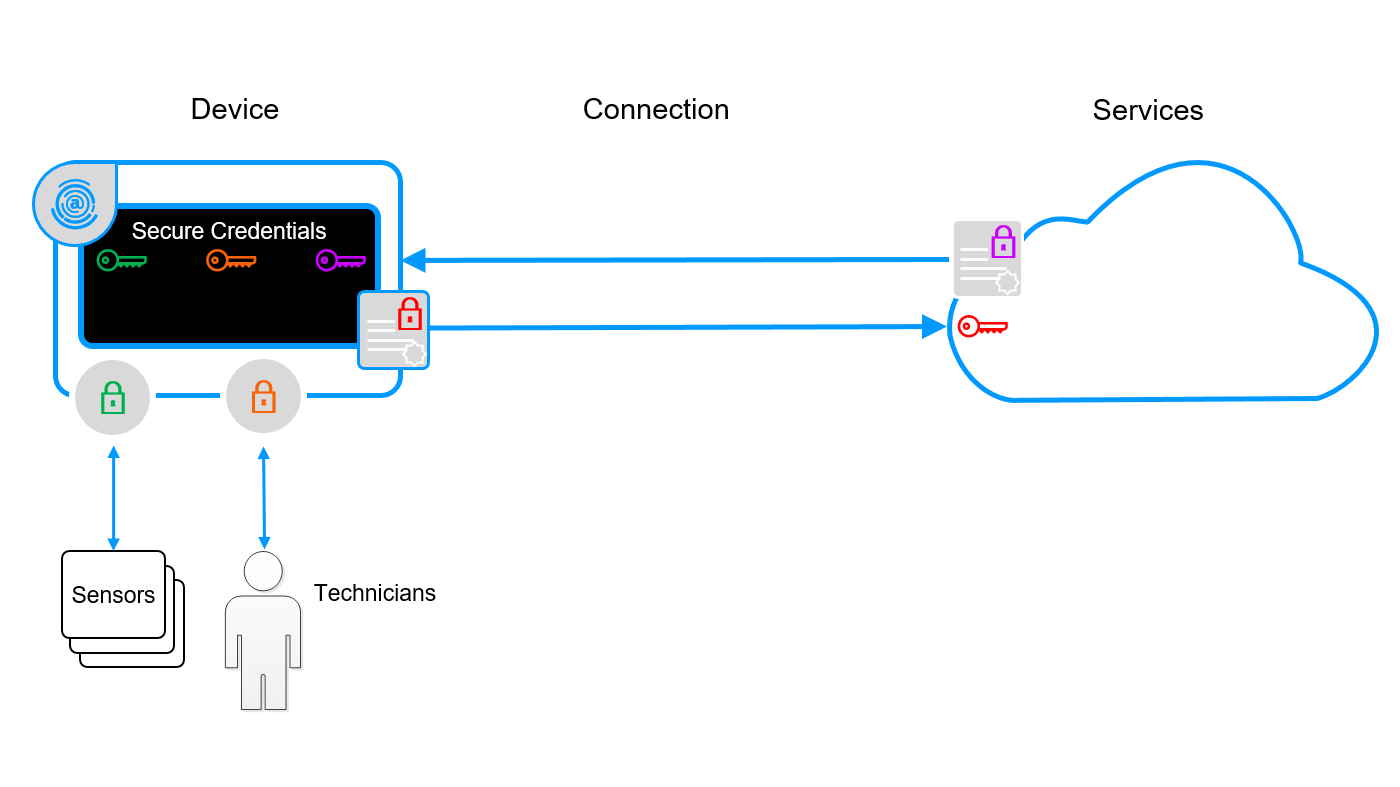
Encrypting credentials in data blobs
Most devices and equipment will connect with external resources such as cloud services, users and sensors. Authorizing controlled access to these resources is usually achieved with credentials such as keys, certificates and other forms or proxies for identity.
Storing these credentials in-the-clear (not encrypted) is clearly a bad idea, so its common good practices to wrap them up securely as an encrypted data blob (binary large object).
Zymbit security modules provide an ‘encrypt data blob’ feature that makes it easy to independently secure each credential and store on an insecure media or SD card.
_______________________________________________________________________________________________