Lifecycle Resilience Stack for Unattended Linux Devices
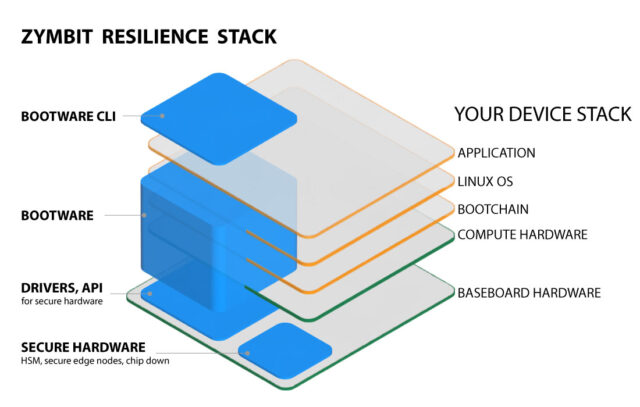
The Integrated Resilience Stack for Edge Devices
The Integrated Stack for Resilient Edge Devices
Build Faster. Deploy with Confidence.
Innovate Faster.
Operate with Confidence.
Build fast. Deploy with confidence.
Make your edge devices less fragile, more agile
Zymbit's resilience stack unlocks the full potential of your Linux devices by reducing update risks, enhancing reliability, and ensuring long-term security compliance.
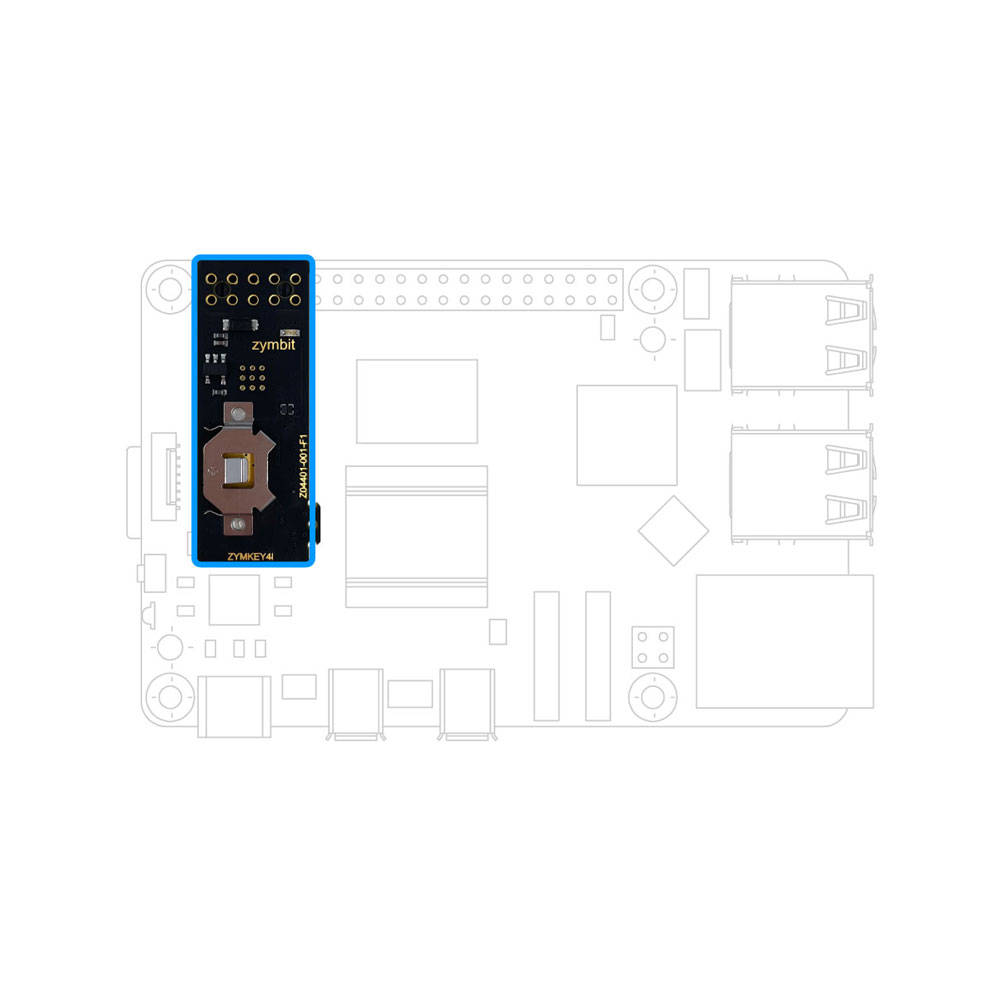
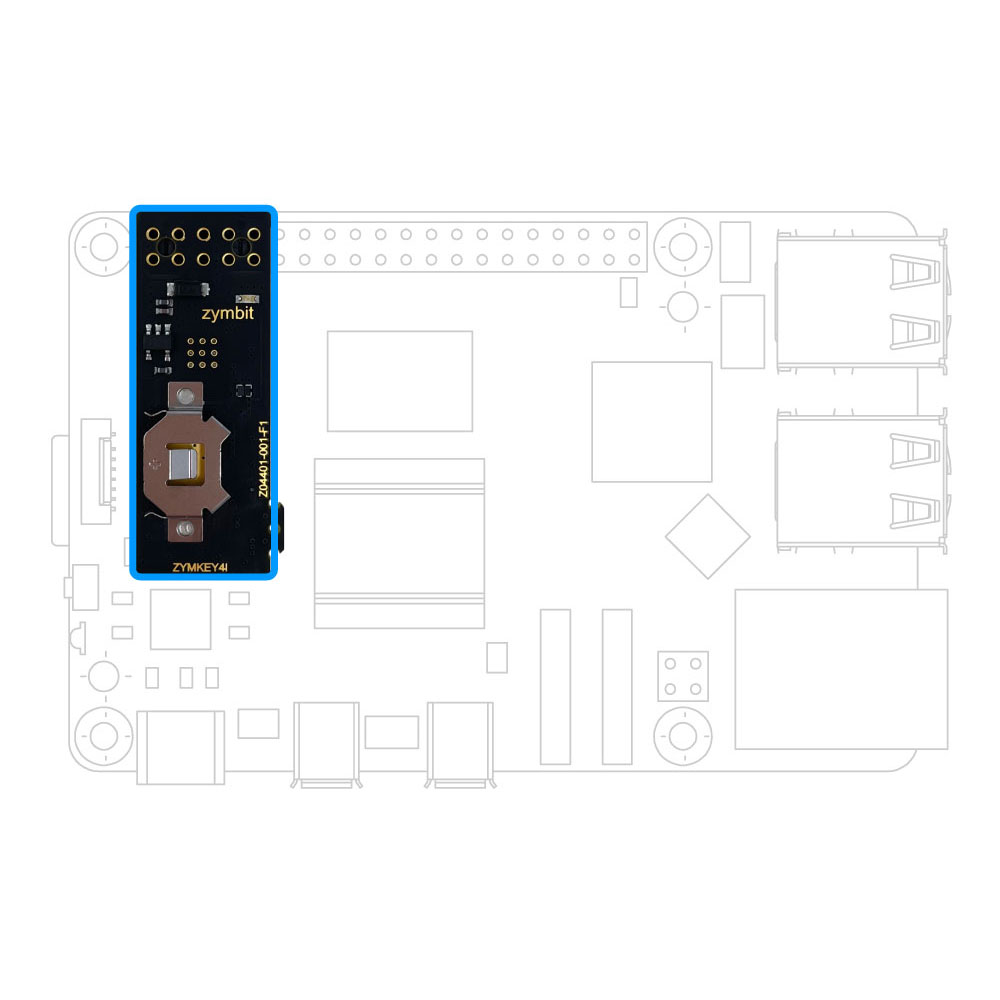
Zymbit embeds lifecycle resilience into every device — with tamper-resistant hardware, secure boot, encrypted storage, and automated recovery — all in a modular stack that integrates seamlessly with your development workflow.
Zymbit delivers tamper-resistant hardware, secure boot, encrypted storage, and automated recovery — all in a modular stack that integrates seamlessly into your development workflow.

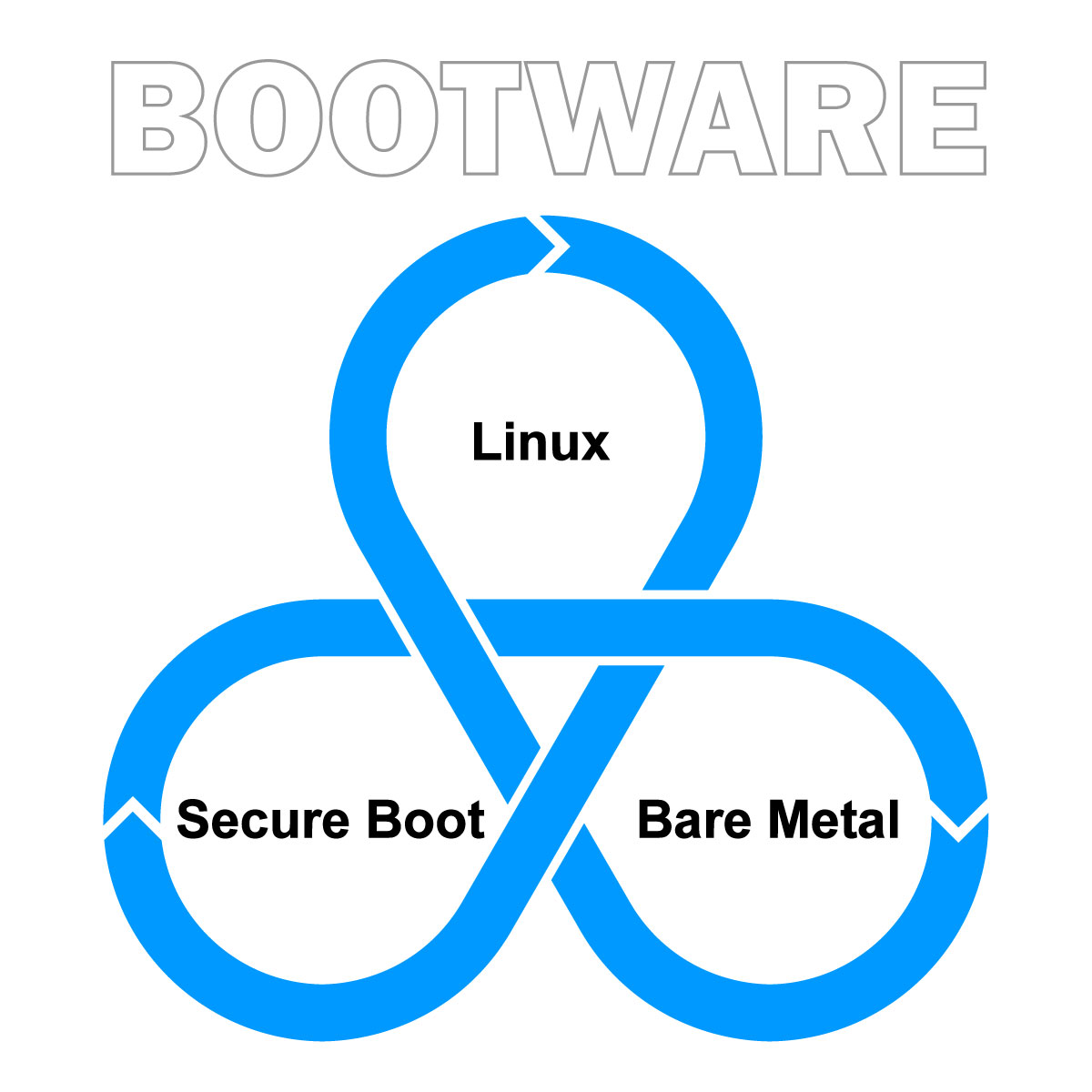
Integrated Resilience Stack for Linux Edge Devices
Secure. Agile. Recoverable
Don’t sacrifice development speed for security or reliability.
Zymbit’s modular stack secures, maintains, and recovers Linux edge devices — integrating seamlessly at any stage of your project.
Don’t trade innovation speed for security compliance or operational reliability—get it all with Zymbit. Our modular stack secures, maintains, and recovers devices across their full lifecycle.



The Zymbit difference
Secure. Agile. Engineered for Life.Lifecycle Resilience for Linux Edge Devices
Unlock the full potential of your Linux edge fleets with a modular resilience stack that integrates seamlessly at any stage — reducing updates risk, enhancing reliability, and ensuring long-term compliance.
Securing Linux devices around the world

Loved by developers

Modular software and hardware that scales smoothly as your device needs grow
Trusted by ops teams

Long term security and reliability managed from your existing ops infrastructure
Trusted core components that scale with your business
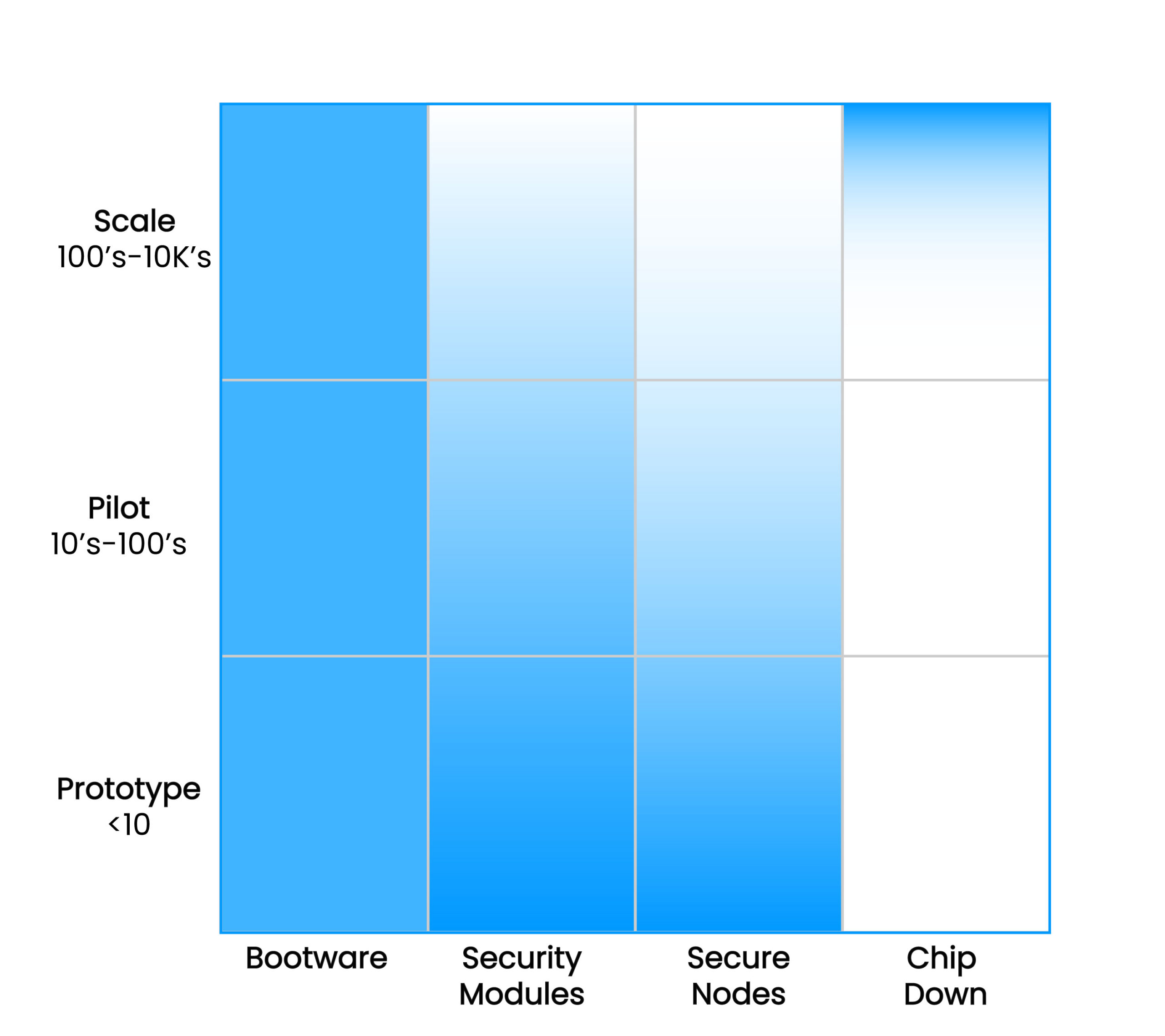
Easy to integrate at any scale
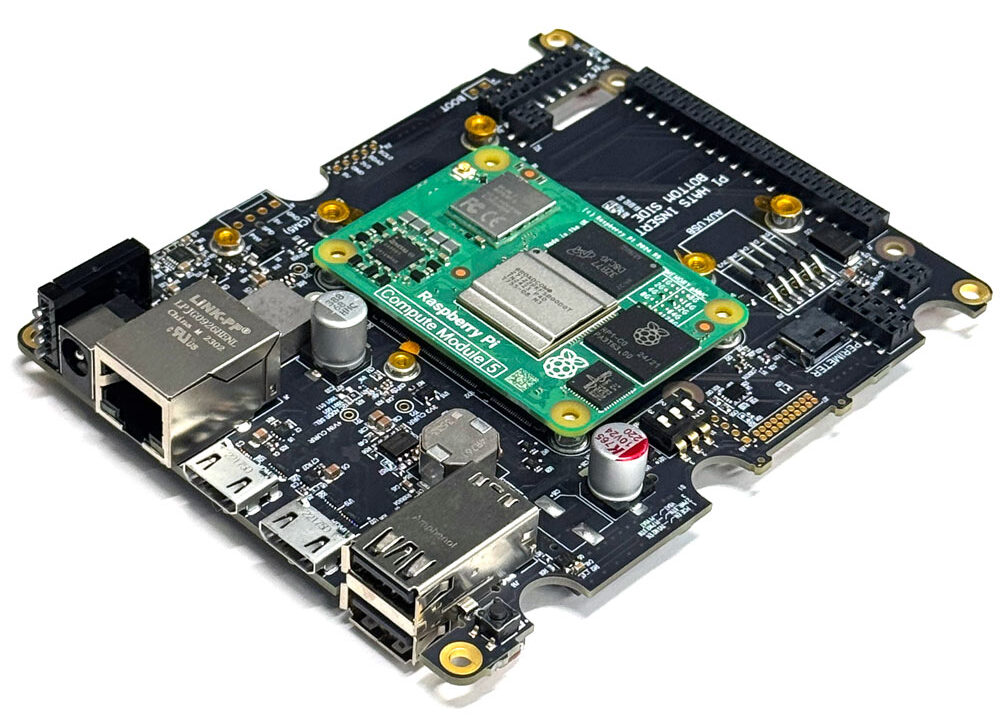
Building core resilience into Linux devices doesn’t have to be complex, or require extensive planning. Zymbit products integrate seamlessly at any stage, deploy flexibly, and scale cost-effectively as your business grows.
Making unattended Linux machines more productive
Making unattended Linux devices more resilient
Build more agile, less fragile, devices and infrastructure
Engineered for life in zero trust environments
Unlock innovation and drive productivity

Adaptive Retail
Smart Retail
enables dynamic customer-personalized experiences, protects identity information

Diagnostic Equipment
protects sensitive information, enables out of band service access for high availability
Factory Automation
protects valuable software IP in zero trust manufacturing environments

Drone Infrastructure
protects critical navigation and communication credentials in drones and traffic managers

On-Prem Key Management
enables application specific cryptographic key management, wallets and services

Agrotech
supports encrypted file system, robust OTA updates and self-recovery
Ways to get started
Ready to get started?
Core simplicity, robust devices
Less complex, more reliable deployments
Simplify device security—maximize reliability
Ensure secure and reliable deployments while maintaining an agile development environment.
Bootware cuts the complexity and risk of managing fleet security, credentials, and image updates. It unifies core device security, resilient updates, and self-recovery in a modular stack—maintained by Zymbit and reinforced with secure hardware.
Bootware eliminates complexity with core security, ironclad updates, and self-recovery—delivered in one unified solution, maintained by Zymbit and fortified with secure hardware.
Bootware delivers core device security, ironclad updates, and self recovery in a unified software solution—maintained by Zymbit, fortified with secure hardware
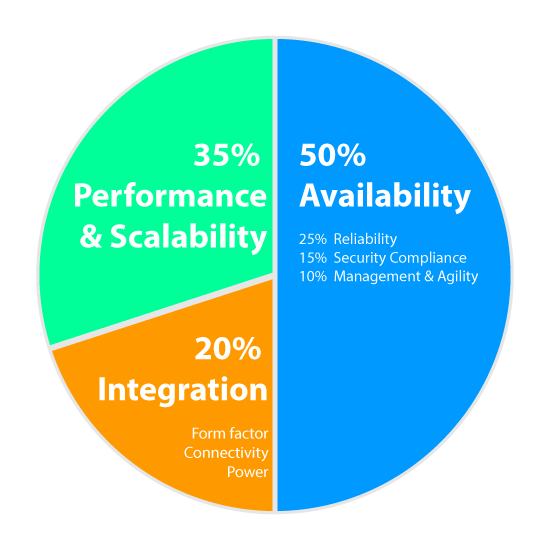
Boost availability, cut service costs, simplify compliance
“Reliability and security are key factors in deciding which equipment to buy”
End users don’t want to manage the complexity of updates and security patches across different compute platforms. They rely on equipment makers and service providers to maintain operational availability and security compliance.
Designed and manufactured in California