Defense in depth
Layers of digital & physical security
Hardware Security & Integrity
Data & Digital Asset Protection
Transaction Authentication & Integrity
Secure technology stack
Layers of physical & digital protection
-
Hardware security & integrity
-
Cryptographic services
-
Secure integrations
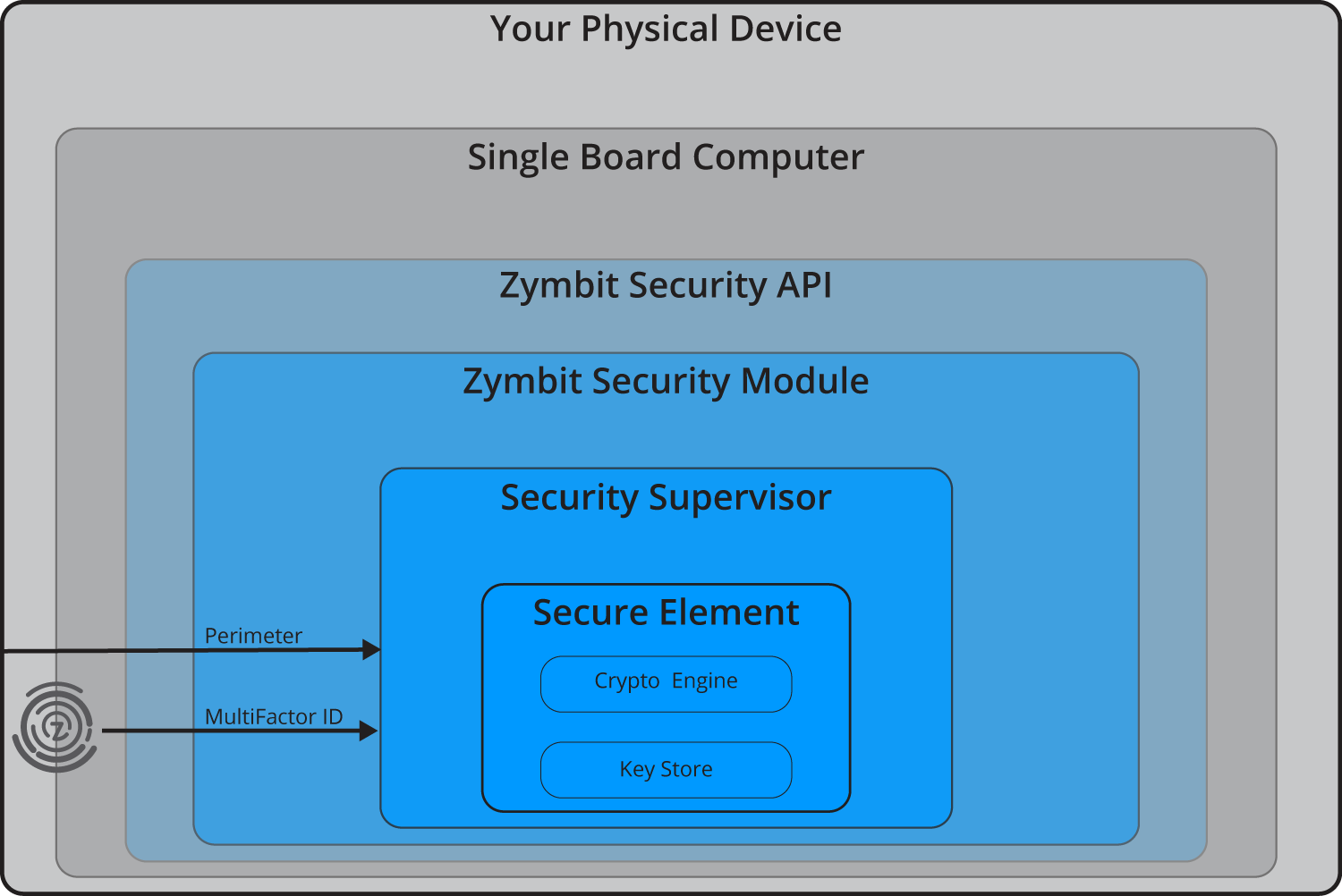
Hardware security & integrity
PHYSICAL TAMPER SENSORS
- Two independent physical perimeter circuits. Learn more >
- Accelerometer for shock and orientation.
- Primary power and battery voltage monitoring.
- Temperature sensors.
- User defined thresholds and response policies.
MEASURED SYSTEM IDENTITY & AUTHENTICATION
- Unique ID created from multiple device-specific measurements.
- Authentication required to activate cryptographic services.
- Permanent and temporary binding modes.
- Custom input factors available to OEMs.
VERIFIED BOOT
Verification of authenticity & integrity of boot, system, application files.
- Available on Zymbit SCM based products.
- Runs on secure MCU, autonomously from RPI.
- Pre-defined file manifest – signed & verified.
- Different failure responses – recoverable, non-recoverable.
- Compatible with popular OTA schema.
REAL TIME CLOCK
An autonomous sense of time helps resist against power and NTP attacks.
- Battery-backed real time clock to support off grid applications.
- 24-48 month operation, application dependent.
- RTC clock service available to client applications.
- Learn more >
SECURE ELEMENT + SECURITY SUPERVISOR
- Multiple layers of hardware and crypto security.
- Dual secure-processor architecture.
- Secure microcontroller supervises access to cryptographic services.
- Secure element delivers crypto-engine and key functions.
ULTRA LOW POWER OPERATION
- ARM Cortex-M0 microcontroller with sub-microamp operation.
- Minimizes EMC emissions footprint.
- Enable years of secure operation from a single coin cell.
- Delivers autonomous physical and digital security.
BATTERY MONITOR, LAST GASP DESTRUCTION
- Continuous on-module monitoring of battery voltage.
- Low or no voltage can trigger tamper event.
- Last gasp policy to destroy key material in the event of battery removal.
- Available on HSM6, SCM products.
ENCAPSULATION & SECURE ENCLOSURES
- HSM and SCM products encapsulated in tough opaque potting
- Standard and custom enclosure types
- Tamper switches, optional tamper mesh
- Fanless cooling eliminates air flow ducts

Cryptographic services and protection
CRYPTOGRAPHIC ENGINE
- Dedicated secure element and security supervisor microcontrollers.
- All services accessible through Zymbit API.
- TRNG service (NIST SP800-22), suitable seed for FIPS 140-2, 140-3 DRNG.
- ECC KOBLITZ P-256 (secp256k1), ECC NIST P-256 (secp256r1)
- ED25519, X25519
- ECDH (FIPS SP800-56A)
- ECDSA (FIPS186-3)
- AES-256 (FIPS 197)
ENCRYPTED FILE SYSTEM + LUKS
- Uses dm-crypt encryption standard
- Automatic integration with Linux Unified Key System LUKS
- Easy to follow tutorial and scripts
- Encrypt hundreds per day with a Zymbit Manufacturing Appliance
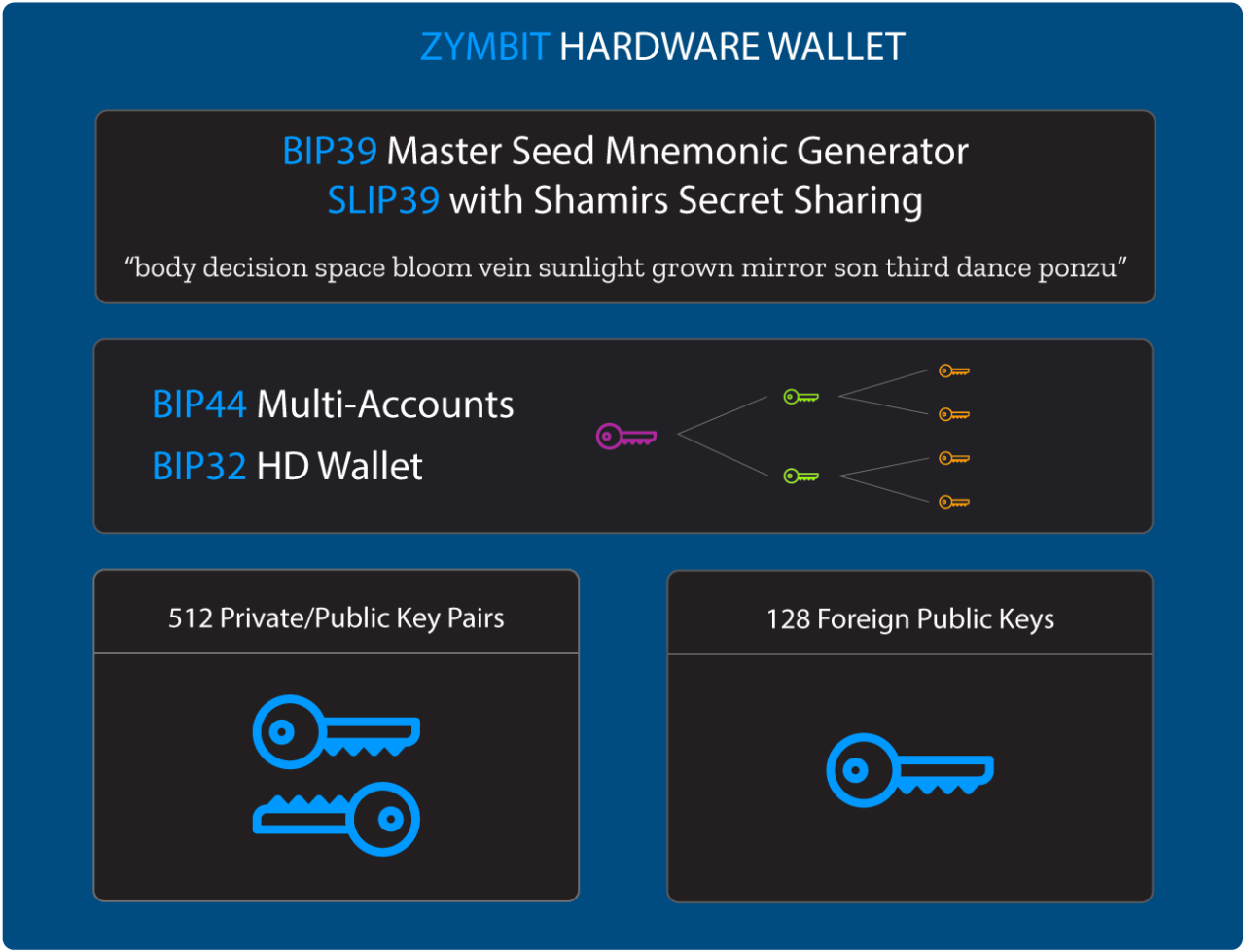
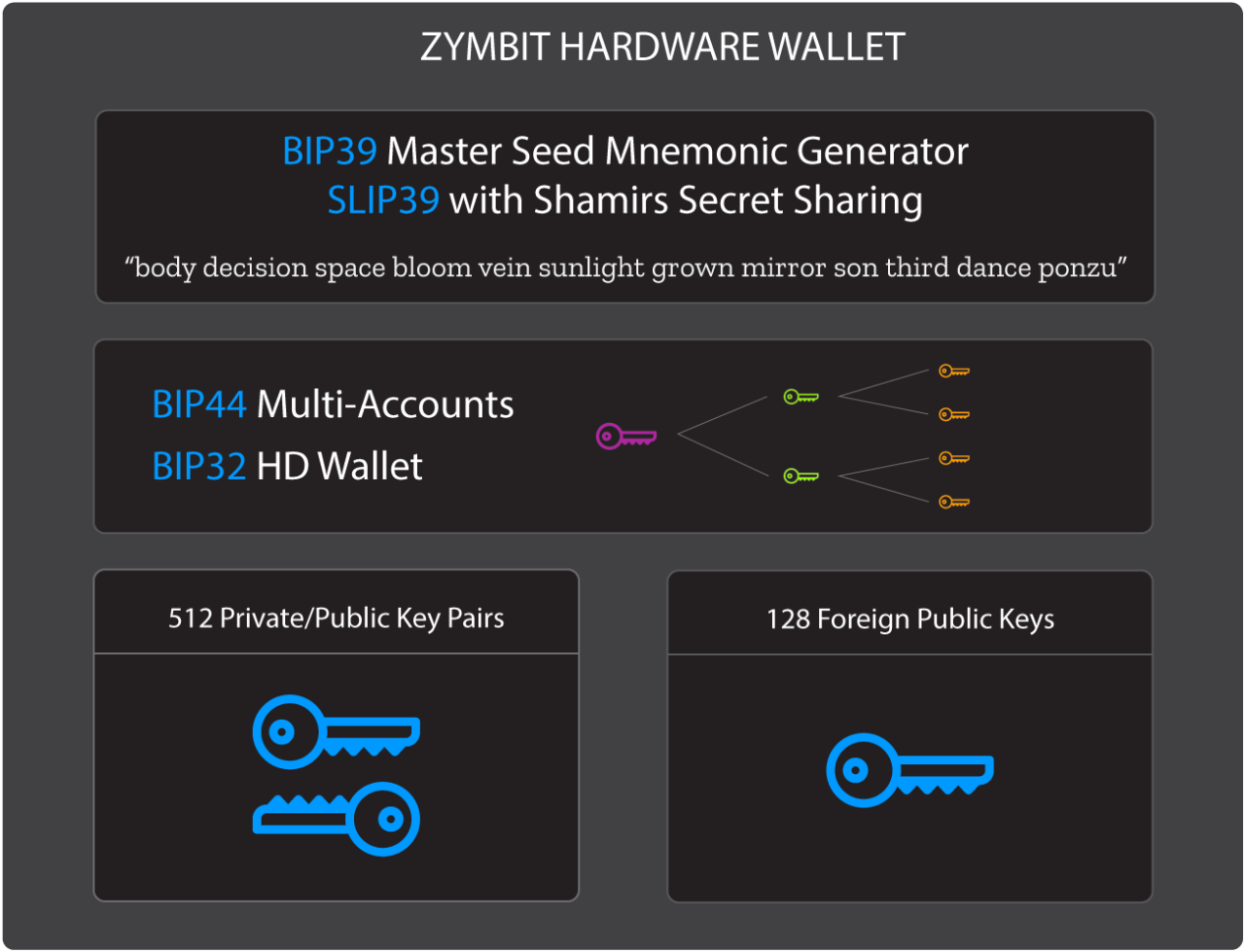
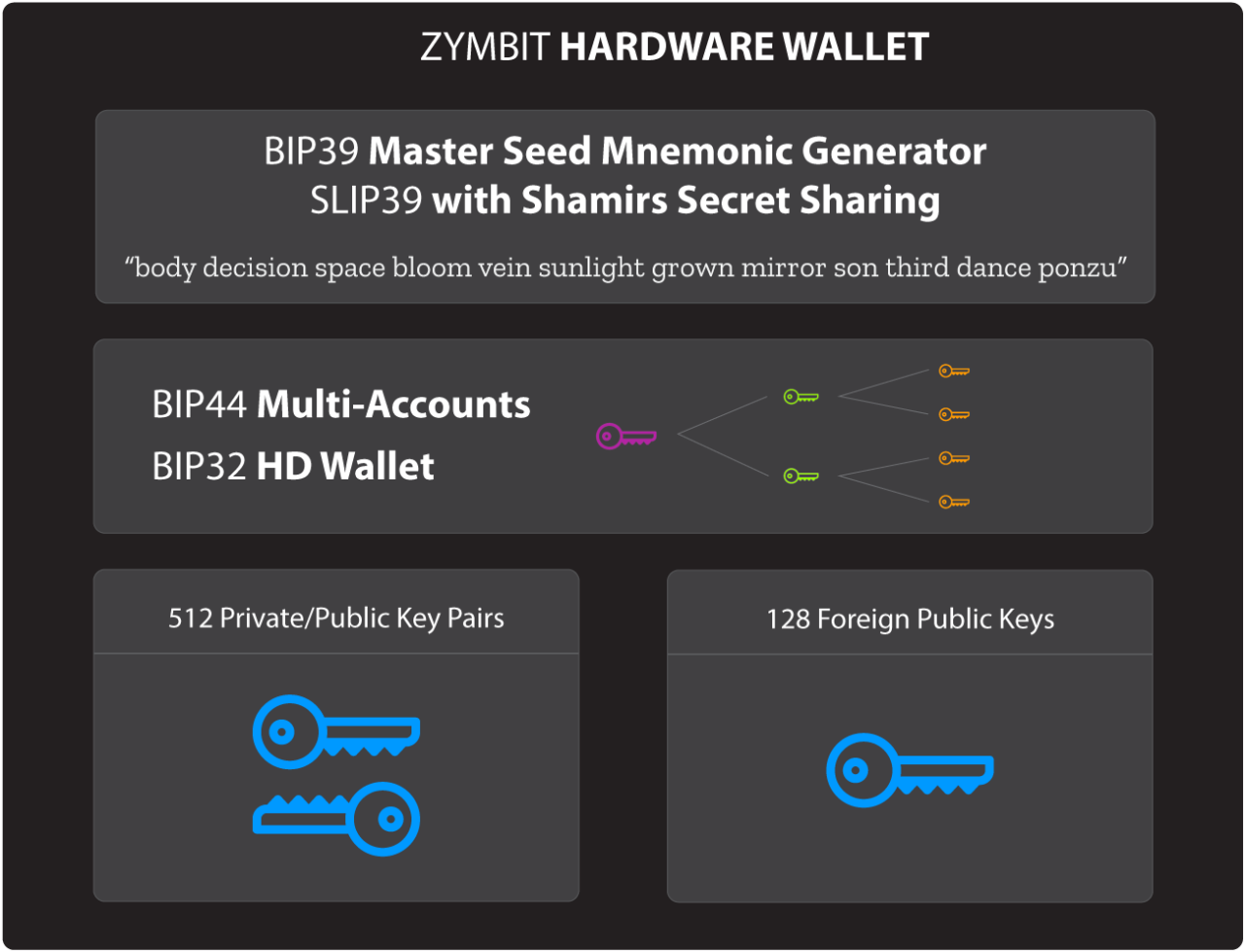
PROGRAMMABLE HARDWARE WALLET
Manage and store hundreds of keys for blockchain and peer-to-peer service connections using industry adopted standards.
- Available on HSM6 and SCM products
- BIP32 HD wallet
- BIP44 multi-account support
- BIP39 master mnemonic seed generator
- SLIP39 Shamir Secret Sharing
- 160 Foreign key slots, user injected
- 512 Private/Public key pairs , internally generated
- ED25519, X25519, secp256k1, secp256r1 (NIST P-256) support
- Learn more >
Secure integrations that save time
Step-by-step instructions on how to integrate Zymbit into your application
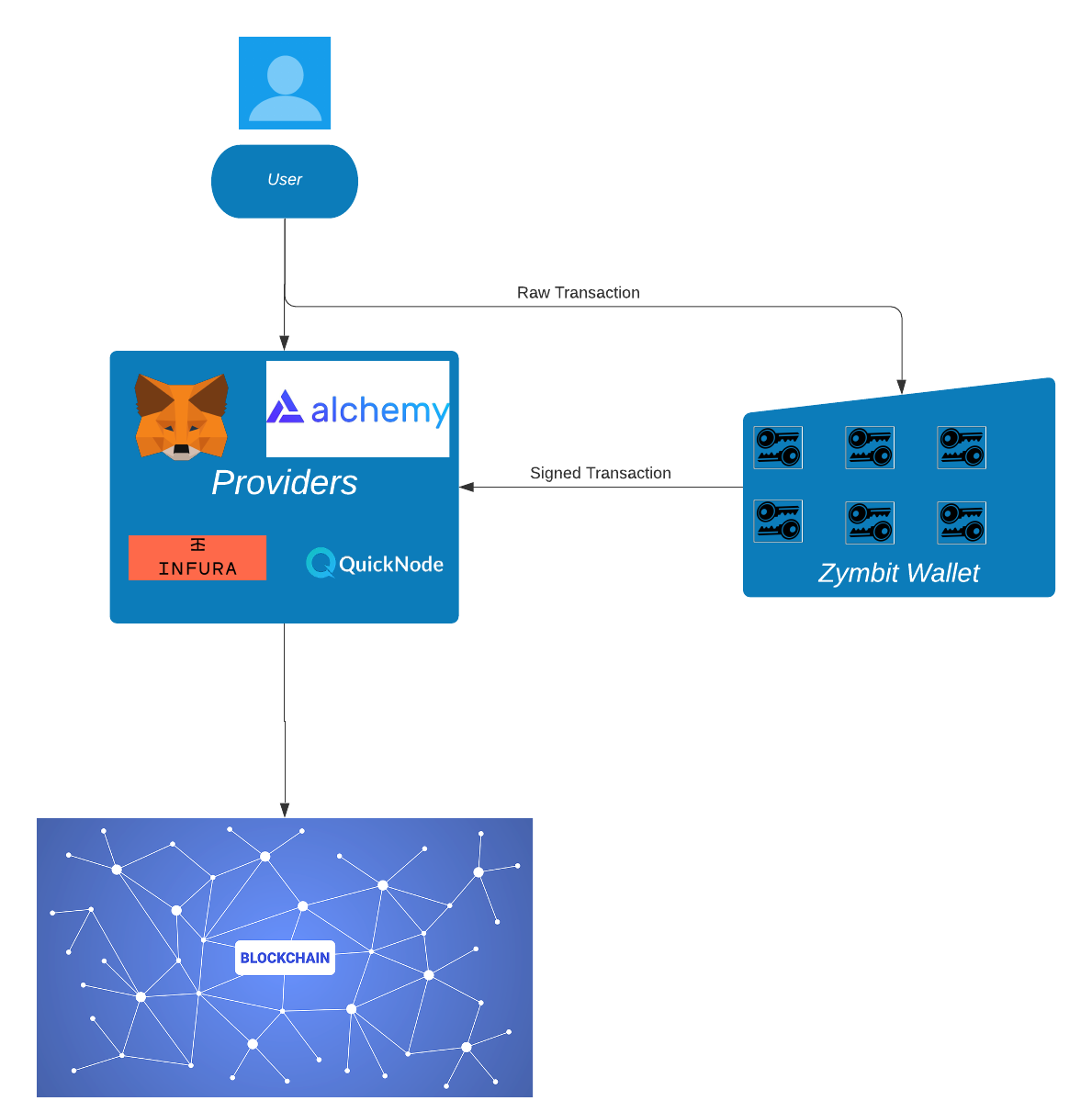
Hardware Wallet Integrations & Examples
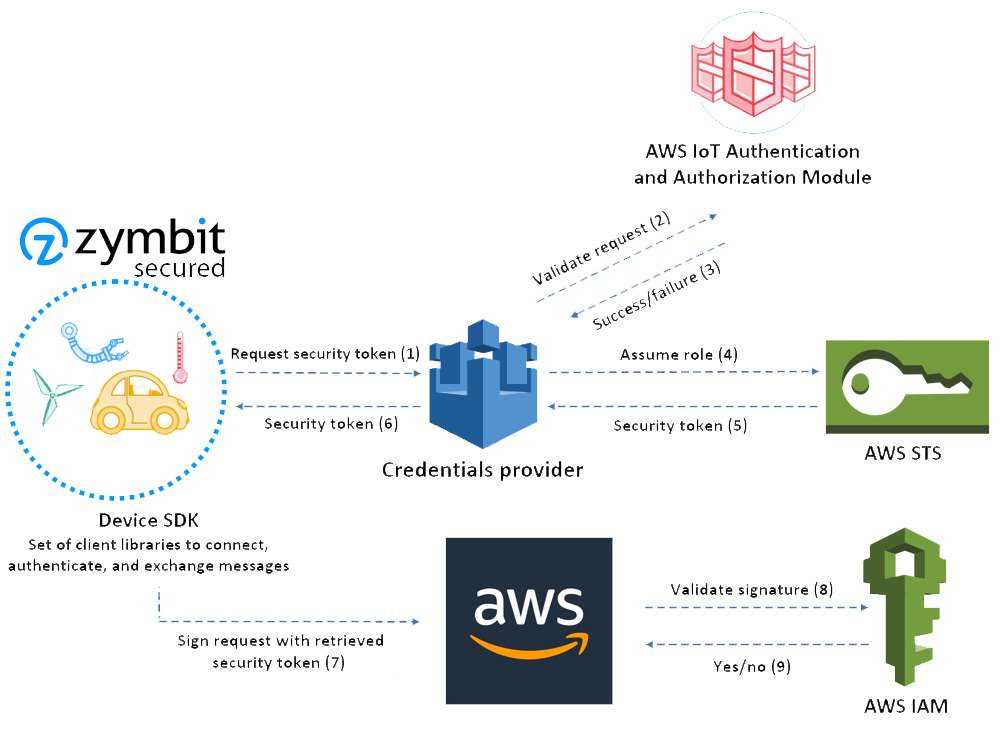
Integration with AWS Credentials & IoT
- AWS Credentials – Integrate Zymbit
- AWS IoT – TLS Client Certificate Authentication
- AWS IoT – Just in Time Registration of Client Certificates

Tutorials that help understanding
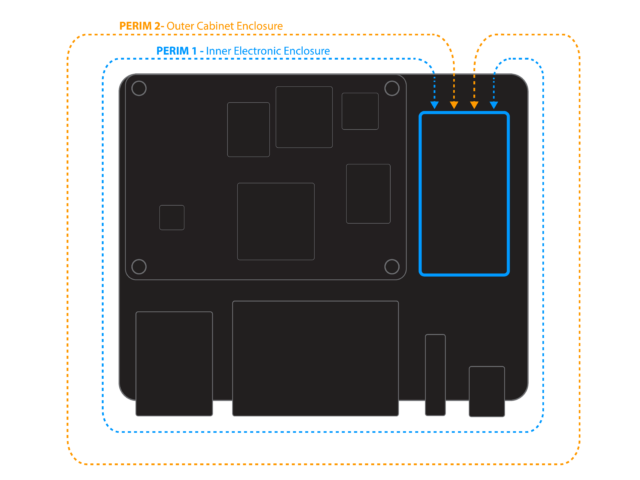
Using perimeter tamper detect
- Two independent perimeter circuits provide layered protection.
- User configured policies and actions.
- Notify or destroy keys on perimeter-breach event.
- Continuous operation with onboard battery.
File system encryption
- Encrypt root file system with dm-crypt.
- Protect data, applications and credentials.
- ZYMKEY integrates seamlessly with LUKS key manager.
- Step-by-step guide with prewritten scripts that streamline the process.

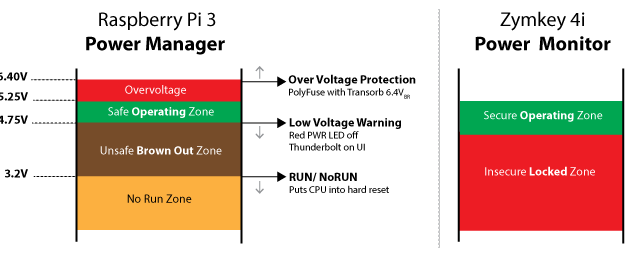
Power quality & security considerations
Poor power quality can result in unstable and potentially insecure operation of compute hardware, depending upon it’s design, operating conditions and related system and power components.
Learn how Zymbit products can help protect your device against common power quality exploits.
Ready to get started?
Explore and choose the best Zymbit product for your application. If you have questions or need something custom then were ready to help.
I'M READY TO BUY
Zymbit products are available from major distributors around the world, or directly from our webstore.
I HAVE QUESTIONS
If you need help with your application, or want to discuss a custom solution then contact us today.



